问题现象:出现用户认证错误(确认密码正确)
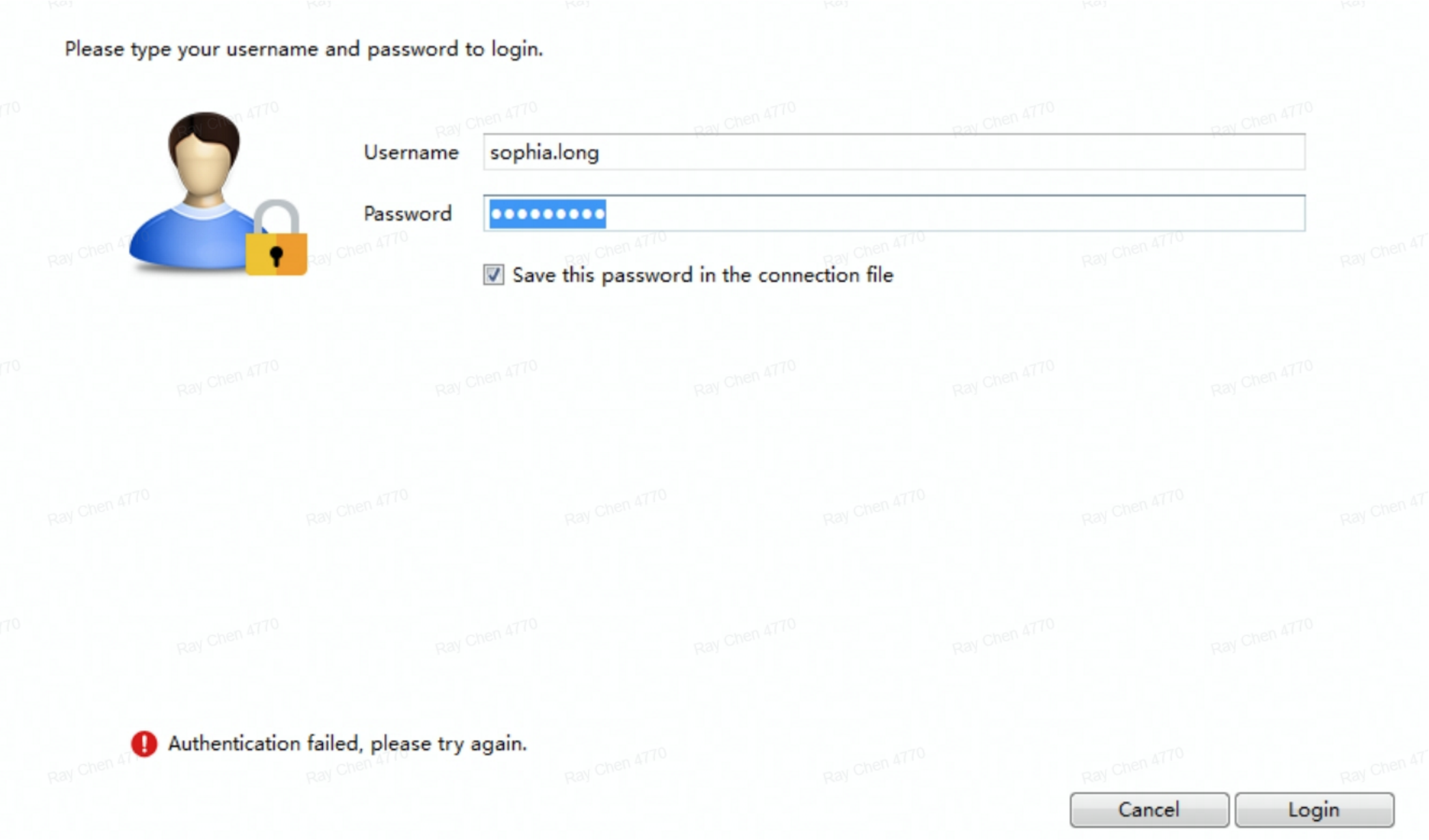
/var/log/secure 提示system error
![]()
/var/log/message 提示 [sssd[krb5_child[18654]: Disk quota exceeded
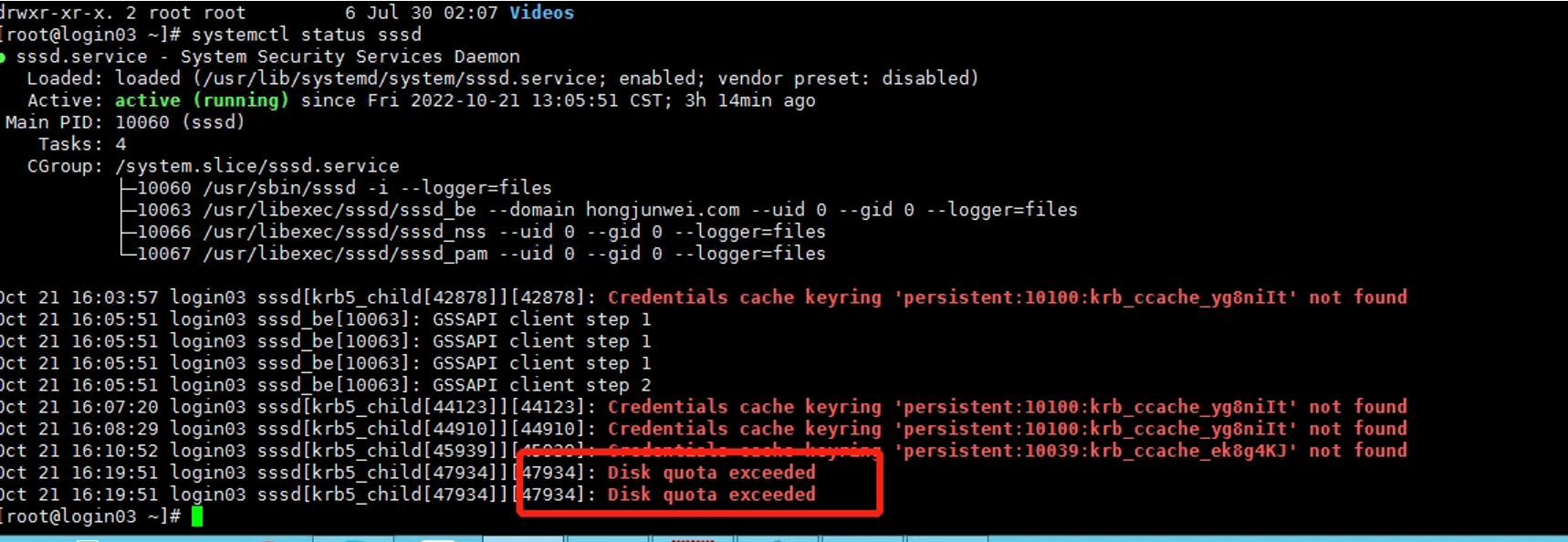

问题原因:
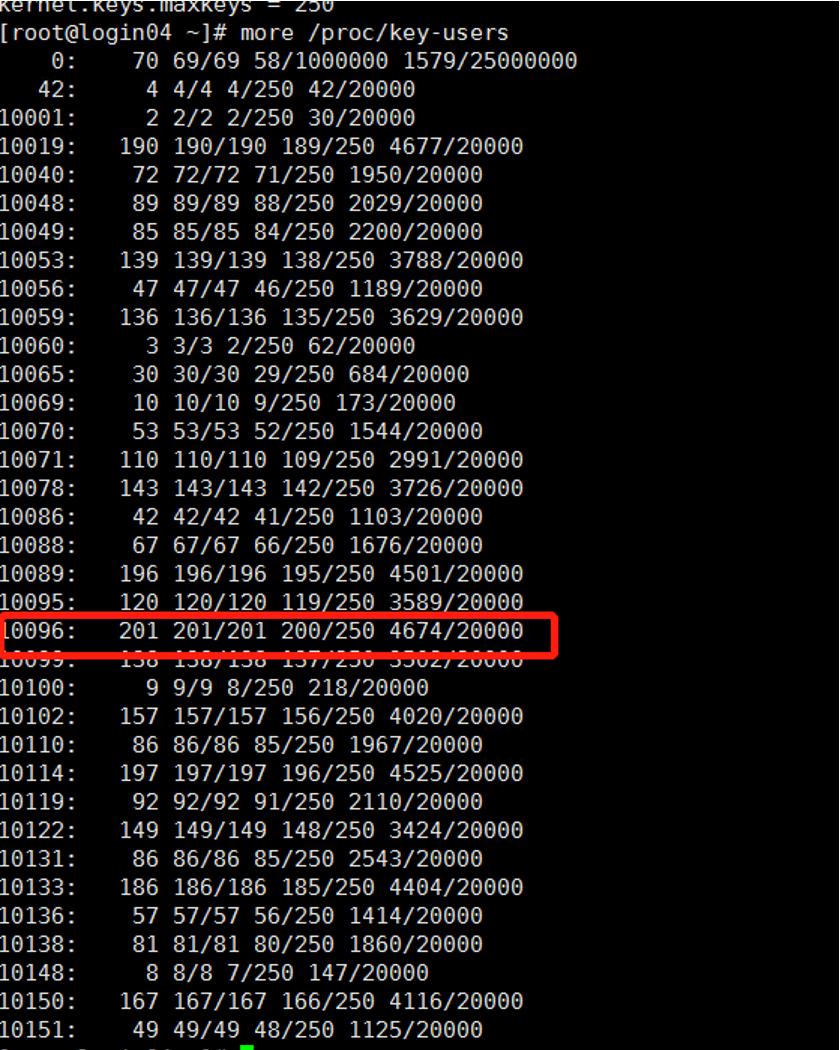
The data is safe in the kernel and is not accidentally written to the hard disk by swapping. However, there is a problem: the mechanism could be abused as a DOS attack if there were no quota mechanism that limits the maximum storage space. And that’s exactly what struck, because the Kerberos keyring has become too large over time. Via /proc/sys/kernel/keys/maxbytesis limited to a maximum of 20,000 bytes per user:
# grep $UID /proc/key-users
2260: 28 28/28 /28/200 18733/20000
解决方案:
调整/proc/sys/kernel/keys/maxbytes 或 /proc/sys/kernel/keys/maxkeys参数
(The meaning of the values is described in more detail in <man:keyrings(7)>.) When trying to authenticate me, the SSSD got a new ticket and wanted to attach it to my keyring. But that failed because of the quota limitation.
This can be changed globally for all users as follows:
# sysctl -w kernel/keys/maxkeys=300
kernel.keys.maxkeys = 300
# sysctl -w kernel/keys/maxbytes=64000
kernel.keys.maxbytes = 64000
After that it was possible to register again. In the statistics I could then see that the storage space was not sufficient:
# grep $UID /proc/key-users
2260: 29 29/29 29/200 20127/64000
This adjustment can be made persistent, for example via a file such as /etc/sysctl.d/sssd.conf, where this change is carried out at every start.